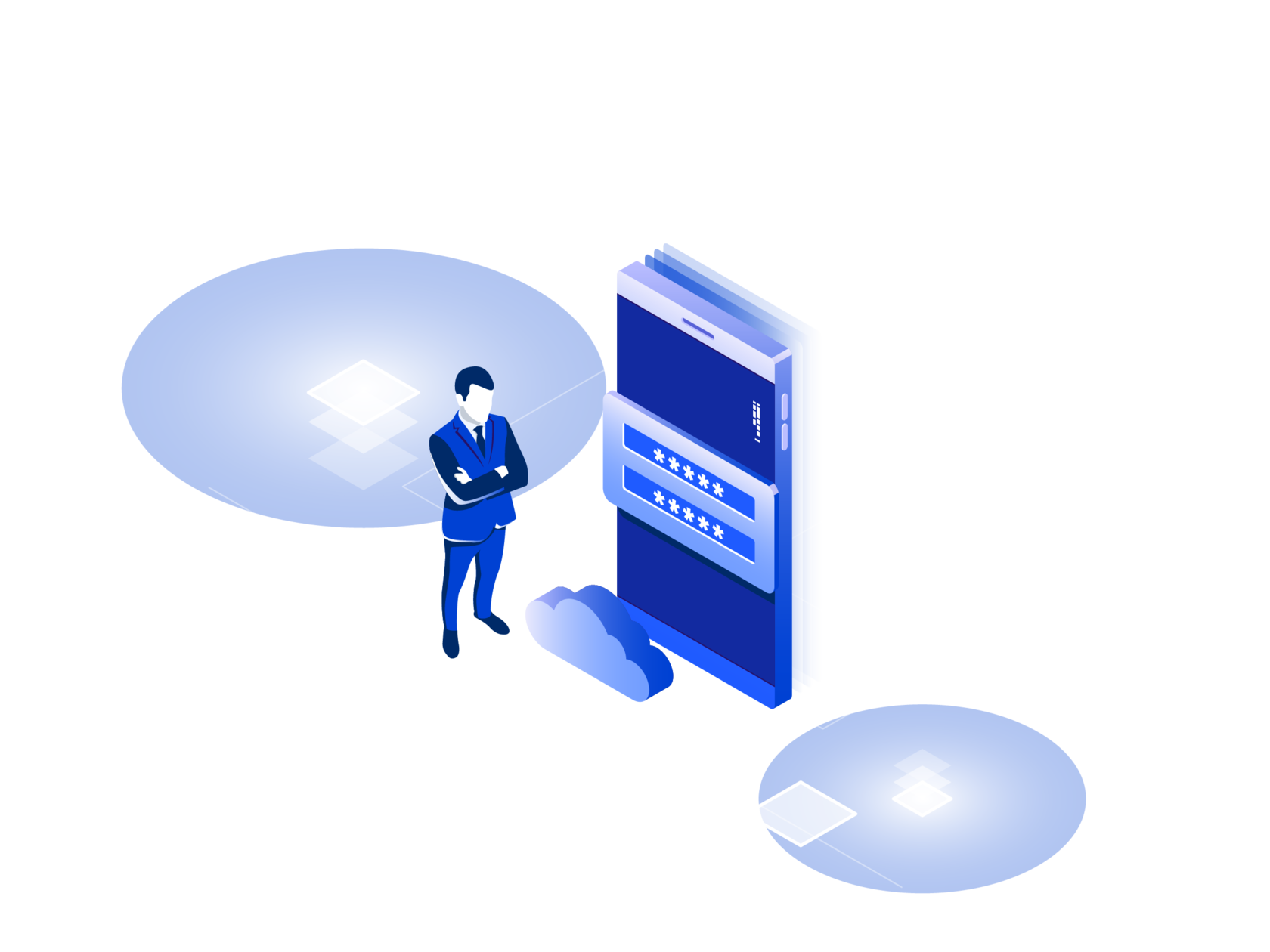
Mobile application testing
Security analysis of IOS and Android applications
SERVICES
Gray Box penetration testing
Outside and inside perimeter testing
Gray Box
This is a method of testing of a mobile application where the functionality is examined through the use of non-public access or other information. At this stage specialists are provided with additional rights to the access. The tests are based on the information given by a client (the authorization data, the algorithm, the architecture, API, etc.)
Our approach is ecological
The testing is carried out by professionals, who will keep your infrastructure safe and identify information security bottlenecks. In the course of the works we check the mobile application, the back end and examine the exchange channels.
All mobile app components check
Data integrity is in safe
Direct support of your developers while eliminating vulnerabilities


Defining
the objectives
the objectives
1
2
3
4
You present the list of applications to be tested
1
2
3
4
1
2
3
4
How does it work?
Identifying
the vulnerabilitie
the vulnerabilitie
We design scenarios of intruders' attacks on the client-side and the server-side examining the exchange channels
Report generation
We describe the identified weaknesses and provide you with detailed recommendations for correction
Double check
After applying the correction plan we do follow-up audit
Get the pentest of your application
We will analyze your application and design an action plan to rectify vulnerabilities

